The emergency for Coronavirus it does not seem to be just a health emergency, although certainly the one that affects the most. As a matter of fact, even on the Web, the numbers increase complaints about false mail, software or even PEC which at first seem true but which are not so true, on the contrary. Email or PEC have been circulating since the Coronavirus emergency started in Italy, which seek to leverage their health emergency by promoting products of dubious functionality but which can be dangerous because they are real malware.
Smart working one of the simplest ways of access precisely for these attackers and it should be remembered that with teleworking, workers are given greater responsibility for the security of their computers. In this case, in fact, it is easy to work on a device that until a few weeks ago was intended for private use, to forget the contextsusceptiblein which you use it (when, for example, we access critical applications and sensitive data), and at the same time difficult to accept restrictions on the use of your own computer, it is necessary to adoptextra security measuresand onemore attention to scams. In this case it is easy to fall into error.
If the passwords are stolen for access to the management software, the PEC mailboxes of the administration or the PC becomes part of an unabotnet, the damage could easily be extended tothe whole company with a series ofcollateral damage difficult to contain(for example, a compromised PEC account often used to attempt to massively infect thousands of other accounts, third party access to sensitive information cannot be canceled, and so on).
What not to install between software, documents and phishing
Some precautions could be decidedly important, if not fundamental, to preserve the integrity of your sensitive data and therefore also those of your company. In this case the suggestions come directly from the Agency for Digital Italy which precisely warns the less experienced workers of smart working.
Let's start with the software first. In this case, do not install software from unverified emails. If an administration or company technician to request the installation of the software via email, carefully check whether the email was expected as agreed with the company and if the sentences written in the email are in correct grammatical form. It is not only good to also check the sender and his address that are correct and in line with the expectations of the company and the technician.
Interesting to remember that for any potential insecurity it is possible to save the email received and attach it to a report directly to the Agency for Digital Italy (to THIS Address: [email protected] or HERE) for an evaluation. In this last period there are really many reports that are arriving on any advertising campaigns on teleworking software that very often are only malware.
As for the documents instead here too it is easy to run into a fraud situation, above all with documentation concerning the times of payments, orders and taxes. It often happens that documents are attached to emails with the most classic Word or Excel file which is more 'friendly' for everyone, especially for the less experienced. In this case, it is important to remember that no Authority or person sends communications with compressed archives or attachments with ZIP, RAR, TAR, GZ extension). Usually the preferred format for PDF or P7M communications, even though these formats (especially the first one) are not totally absent from bad surprises but more difficult to conduct a complete attack.
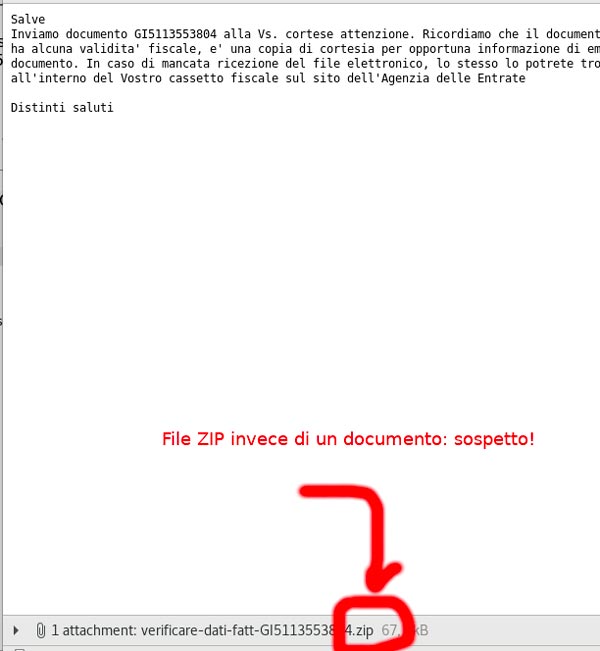
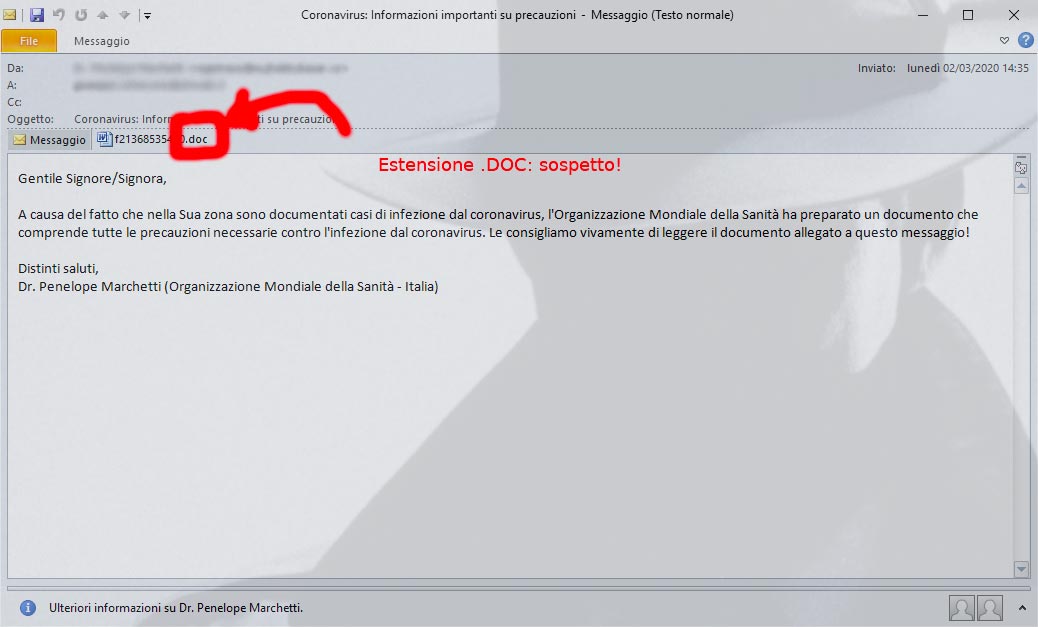
If the attached files are instead simple documents in Word or Excel here it is important to check that they are with DOCX or XSLX extension and not with the more "malicious" and less secure DOCM and DOC or XSLM and XSL extensions. In this case it often happens that for the second and third versions, the attacker has hidden a dangerous malware for those who will open it.
Click to enlarge
Finally also the phishing once again it is a form of intrusion by the attackers of the Web. So far there have been no reports of situations attributable to Coronavirus or of the last periods but it is not difficult to imagine that the theme of the Emergency can not be used also in e-mail of phishing. In these cases necessary be careful never to enter the username and password used for work on sites or programs other than those of the administration or company.
In THIS page can find a lot of information about just the malicious situations in this period of Coronavirus.















