GPU, a new ally for malware: an unprecedented danger on the horizon?
the GPU, and more precisely theirs buffer in memory, could soon become a new weapon in the hands of the malicious people they want attack PCs to steal sensitive information.
As reported Bleeping Computer, at the beginning of August of the code proof-of-concept (PoC) useful to take advantage of the GPU was sold on a hacker forum. In a short post, we read about a “technique that escapes the scanning of the RAM by antivirus. [La tecnica] allocates address space in the GPU memory buffer, inserts and executes code from l “.
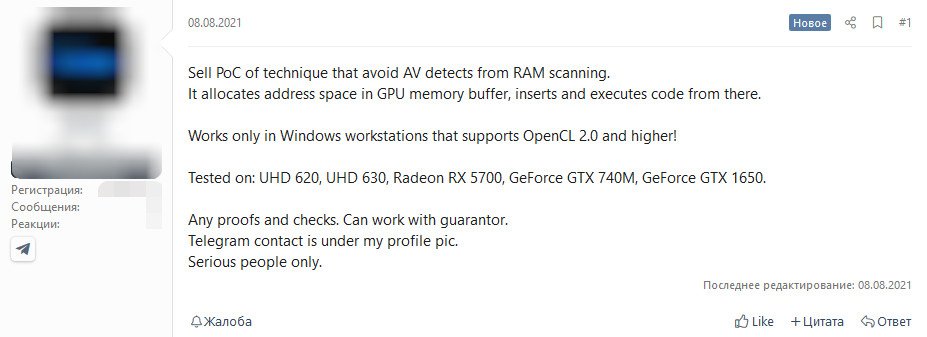
Fonte: Bleeping Computer
The code vendor claims it works on Windows workstations that support OpenCL version 2.0 and above. In the post some GPU models are mentioned, including integrated solutions in the processors and dedicated video cards, on which the technique has been successfully tested: Intel, AMD and NVIDIA, no one seems to be missing.
Though in the academic world there has been talk for several years about methods to exploit GPUs in this way, and PoCs have even been published, until now the projects had remained largely confined to that sector or had never been refined to hit on a large scale.
In the past, in 2015, JellyFish, a rootkit GPU, was released “Linux based“and the same creators spread the PoC for a keylogger and a trojan for Windows always able to exploit the GPU. The new danger does not seem to be connected to JellyFish.
The post tracked by Bleeping Computer was published on August 8 and according to the seller the PoC was sold after about 2 weeks, on August 25, for an unknown amount – just as the identity of the buyer is unknown. According to VX-Underground, the malware “allows binaries to run from the GPU and in the address space of the GPU memory, rather than the CPU”; a demonstration of the technique should arrive “soon”.
















