The growth of the money supply in many crypto projects is provided by miners, while crypto mining not only provides emission, but also is the main element of protecting the peer-to-peer network. A digital printing press works strictly according to a given algorithm, it can only be changed by universal suffrage of network participants.
The sha256 algorithm, on which the mining of the patriarch of the bitcoin cryptocurrency is based, was not created out of the blue. It is based on the SHA-2 hashing algorithm used to create data transfer protocols in the global network (TCP / IP). The sha256 algorithm is one of the SHA-2 hash functions. In this review, we will tell you how sha-256 mining works and what are the pros and cons of this crypto protocol.
What is SHA-256
SHA stands for “safe hash calculation“. With this computation method, cryptographic datasets are protected. Indeed, without a special code, which only the owner has, it is impossible to gain access to encrypted information. The SHA-2 algorithm, of which SHA-256 is a subspecies, was developed at the beginning of the third millennium by the US National Security Agency. The number 256 indicates the number of fragments that make up this cryptographic code.
A few years after the release, the Agency patented the second release of the SHA-2 algorithm under license Royalty-free, thanks to which the technology could be directed to a peaceful channel.
Protocol features
There is no single method for optimizing the selection of the hash sum. The SHA-256 protocol, accepting certain ones, produces an absolutely unpredictable result. The search for the desired option is performed by a banal enumeration of all possible combinations. Choosing the right hash is a matter of chance, but the more power of the computing equipment, the higher the chances that you will find it faster than the rest of the participants in the process.
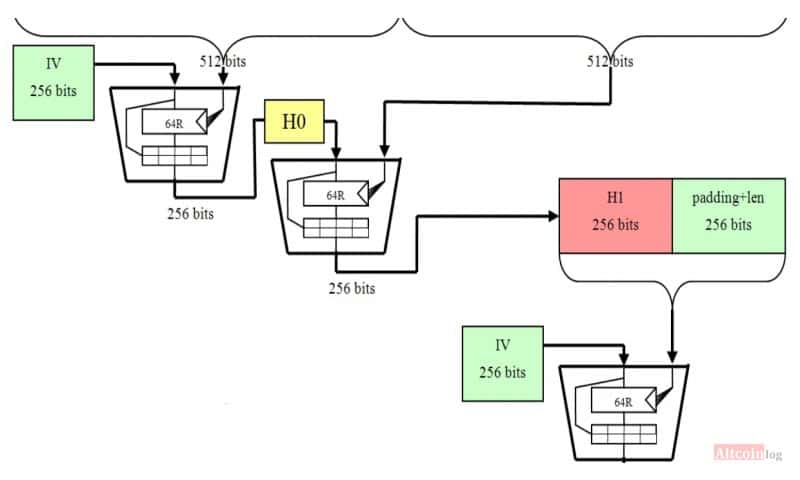
For the sake of completeness, let’s add some complex technical information. In the SHA-256 protocol, data is fragmented into 256 slices, each containing 512 bits (64 bytes). The shares are mixed according to a certain cryptographic scheme, which is embedded in the algorithm, and as a result, a special hash code of 256 bits is formed. Mixing information is repeated 64 times. I must say that this is not so much compared to the new cryptoalgorithms.
SHA-256 technical parameters:
- Information block size: 64 bytes;
- Allowed length of one message: 33 bytes;
- Block hash signature size: 32 bytes;
- Number of mixes per round: 64;
- Network data transfer rate: about 140 MiB / s.
The algorithm is based on the technique Merkel-Damgard, the array of information is divided into separate blocks, each of which has 16 parts. After performing 64 shuffles, the system outputs the correct hash sum, which serves as a starting point for processing the next block. The process is continuous and interconnected, it is absolutely impossible to obtain the code of a single cryptoblock without data on its predecessor.
How hashing works

Hashing – this is a conversion according to a predetermined scheme of any amount of incoming information into a digital code. The outgoing value is unique, with its help it is always possible to identify this particular array of information. The algorithm for creating an encrypted string (hash code) is called a hash function.
A valid number in the encrypted signature line of the bitcoin cryptoblock must contain a certain number of zeros. At the time of compiling the review, the number of zeros in the hash code of digital gold had already exceeded the number 17. Therefore, decoding sha256 is more difficult than finding a certain grain of sand located at an arbitrary point on the globe.
Important! In principle, you can encrypt anything you want, even a poem by Lermontov “Prisoner of the Caucasus“And the result is a hexadecimal code like: c8ba7865a9x924590dcc54a6f227859z.
Encryption has no retroactive effect, it will not work to make text from an alphanumeric set, but if at least one dot or space is changed in the poem itself, then the hash code of the work will be completely different. You can see for yourself by visiting the site for automatic encryption http://crypt-online.ru/crypts/sha256/.

Block dependency in the bitcoin network
In the network of each cryptocurrency, including bitcoin, blocks represent an array of information about transfers of funds for a certain period. Each of them has a unique hash code (signature).
As already mentioned, the cryptographic signature of the subsequent follows from the hash code of the previous one, forming an integral system in which nothing can be changed or faked. Miners are constantly busy calculating the signature of a new block, and are rewarded only for the result.
Coin list of SHA 256
SHA-256 is a classic cryptoalgorithm. In addition to the first cryptocurrency Bitcoin, 43 more blockchain projects are based on it.
Most Popular:
- Bitcoin
Cash; - Bitcoin
SV; - Litecoin
Cash; - Peercoin;
- DigiByte.
The full list is available on the website Miningpoolstats.stream.
Pros and cons of the algorithm
The main advantage of the SHA256 algorithm is its relevance. We can say a hundred times that this protocol is morally outdated, but so what? Although SHA256 is not particularly aesthetic, it is cheap, reliable and practical.
However, there are also downsides. First of all, this is the gradual loss of decentralization. Industrial companies control huge data centers and large amounts of virtual coins, while small miners get crumbs. Alternative crypto projects are taking measures against the dominance of ASICs, but in SHA256 everything goes on as usual.
Conclusion
At the end of the article, you need to apologize to the reader for an overly complex explanation of the topic, but, alas, the story about the basics of cryptography cannot be classified as everyday reading. As for the prospects for SHA-256, while bitcoin occupies the lion’s share of the market, this algorithm will be in great demand.
But if the patriarch of digital assets is supplanted by alternative projects running on other algorithms, then SHA-256 will become the property of historians. And such a turnaround will only revive the blockchain industry.
Subscribe to our resources and read comments, sometimes smart people write smart things there.
Related materials: