A hacker very determined to achieve his goal often able to develop very imaginative and equally effective methods although for the most part it is sufficient to leverage bad security practices or software vulnerabilities to succeed.
Those who have built a reputation for identifying very particular, but still exploitable, hacking techniques are the researchers of Ben Gurion University of Israel, coordinated by Dr. Mordechai Guri, who focus their research activities on Air-gapped PCs what are isolated from the Internet and not even connected to a local network.
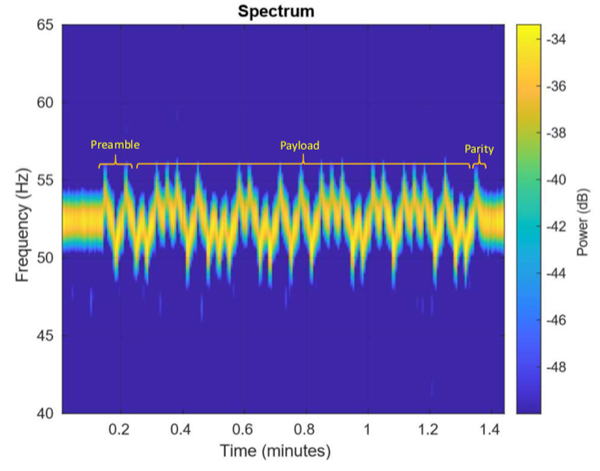
The researchers' latest experiment focused on a technique they developed which is called AiR-Viber. The basic concept that the vibrations produced by the electro-mechanical components of a computer – the fans, mainly – can be used to transmit information, exploiting a malware that can encode the data to be transmitted and manipulate the fans to create the desired vibrations .
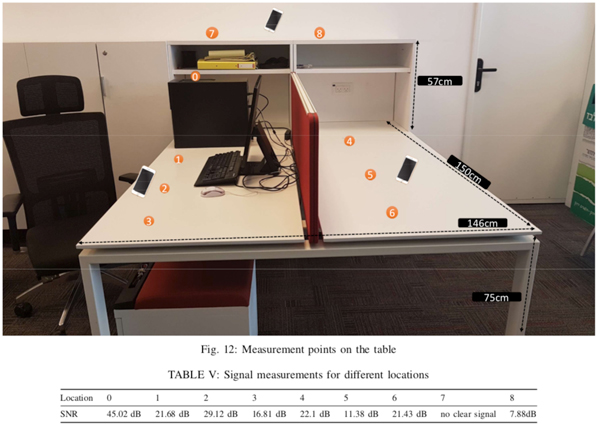
In the experiment, the researchers used a smartphone placed on the same table as a PC to record the vibrations and their variations, taking advantage of the accelerometers of the phone which in today's smartphones are sensitive and precise enough to capture even the most minute variations. In the specific case, the researchers used a Samsung Galaxy S10equipped with accredited accelerometers with a resolution of 0.0023956299 meters per second square.
Be it Android or iOShowever, it is interesting to note that neither of the two operating systems asks for the user's permission to read the data collected by the accelerometers, which in other words means that there is no visual indication such as to make one suspect that something is happening behind the scenes. In addition, reading this information can be done in a fairly simple way, without compromising the mobile device in any way: just use a web browser with JavaScript.
The data transmission tests have had positive results with the smartphone placed about one and a half meters from the target PC. However the incredibly slow transmission speed, in the order of half a bit per second! The researchers then observed that the case fan appears to be the most effective for the purpose, while the CPU fan was found to be less useful.
As previously mentioned, the Guri team has already experimented with ways to extract information from air-gapped systems, and all their companies are summarized on this page. Noteworthy are those of USBee, of which we had already spoken in the news "USBee, the malware that can extort data even from non-connected computers", or even a technique that provides the possibility of subtracting information by acknowledging the changes, suitably induced, of the brightness of a PC monitor.
These are precisely imaginative techniques, probably some more viable than others in the real world, but all converging on a consideration that has become a famous maxim in the world of computer security: the only safe PC a PC that is turned off.















