For two years now, that is, since the attacks Specter and Meltdown CPUs have become public, Intel it "ended up on the grill" with regards to safety of its processors and the various related aspects (firmware, software, etc.). The theme is of particular importance especially in the data center and for this reason the company last year has doubled efforts to regain the trust of its customers.
This is a process that obviously will bear fruit in the long run, but already in 2019 Intel's renewed approach has started to pay off. The company released a report explaining how the internal security team managed to identify approximately 60% of the vulnerabilities that emerged related to Intel products. It is 144 out of 236.
The most interesting data though is that of the remaining 92 holes discovered by external researchers, 70 were reported to the company through the "Bug Bounty" program, set up precisely to stimulate external researchers to report vulnerabilities in exchange for cash recognition (it is a common practice in the software industry). Fortunately none of the 236 vulnerabilities discovered in 2019 were actively used.
Click to enlarge
It is therefore evident the effort to run for repairs by working on both software and hardware, although obviously to make some of the problems that have emerged a bad history of the past more efforts will be needed on the software and hardware front. The competitor AMD, affected to a much lesser extent by problems such as Specter, Meltdown and the like, has somehow shown that there are design choices that allow to combine performance and safety.
One of these is called Full Memory Encryption, implemented through solutions such as SME (Secure Memory Encryption) and SEV (Secure Encrypted Virtualization) in EPYC processors. What is it about? It is a hardware-accelerated protection system that allows the encoding of data in use stored in memory.
In EPYC CPUs the system uses an AES-128 encryption engine integrated into the memory controller that automatically encrypts and decodes the information in the main memory when an appropriate key is provided. The processors then have a chip called the Secure Processor which guarantees cryptographic functionality for the management and generation of a secure key.
During the Security Day organized by Intel during the RSA Conference 2020, one of the top executives of the dataceter division, Anil Rao, explained that the company also intends to adopt Full Memory Encryption for its future processors.
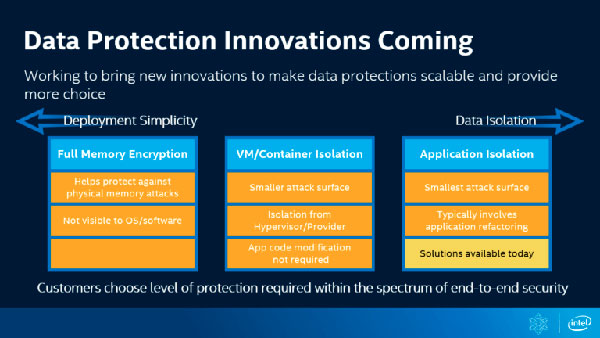
Specifically, Intel is developing solutions such as TME (Total Memory Encryption) or MKTME (Multi-Key Total Memory Encryption). Work is already underway, so much so that last May Intel released a set of patches intended for the Linux kernel related to these security technologies. The problem is that none of its processors currently offer them and it is not known when they will.
From 2015 onwards several Intel CPUs integrate SGX (Software Guard Extensions), a technology designed to protect memory areas from unauthorized users. A process is therefore able to create an enclave – a closed fence – encoded by the hardware inside the memory. The data present in the enclave can only be deciphered within the CPU and the process is triggered only if required by instructions carried out in the enclave itself. Intel SGX is an important security system, but apparently it will only represent a piece of a bigger picture.
In short, while the past cannot be rewritten and existing architectures cannot be changed, Intel has for the future put security at the center, without having trouble looking into the "neighbor's garden" if the solutions put in place represent a useful barrier to threats.
















