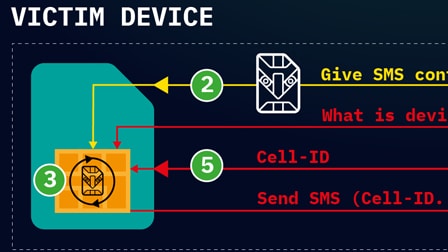
It was discovered in recent days by the security company AdaptiveMobile Security, and it is a really serious threat to the world of cell phones and beyond. It’s about Simjacker, an attack technique that allows, in fact, to take control of a cell phone simply by sending an SMS. The technique uses a communication interface that was originally designed to be used by network operators to communicate directly with customers’ SIM cards and to provide specific or value-added services, such as residual user credit. The problem that through this communication interface the attacker can perform various actions on the phone and with the victim’s phone, such as making calls, sending messages and much more.
Simjacker, a really serious threat
Why did we talk about “serious threat”? It is easy to say: the Simjacker technique can be successfully exploited against a large number of connected devices: not only mobile phones and smartphones, but also IoT devices that require the presence of a SIM card inside them. It is a “platform-agnostic” attack (what does not depend on a specific type of hardware or software) and there is practically nothing the user can do to take cover and moreover the attack, as we will see just beyond, completely transparent to the user who can in no way notice that he has become a target.
AdaptiveMobile Security believes that this technique has been used for at least two years by a “particularly sophisticated” actor, in various countries and for surveillance purposes, probably with the collaboration of government realities. It would not be a mass surveillance campaign, however, as much as an action aimed at the shadowing / espionage of a large number of individuals of any particular interest. According to what the security company says, in fact, most of the cases in which the technique was used only for the purpose of tracing the geographical position of the device, with the transmission of the unique IMEI code.
How the Simjacker technique works
The principle on which this fairly simple technique is based (although its practical implementation requires a series of in-depth knowledge, which is why security researchers have reason to believe that there is a particularly sophisticated group behind Simjacker): it is sufficient to send a SMS specially formatted and containing precise instructions, so that a direct communication channel can be opened with the SIM card, which will respond to the message by sending the IMEI code and the location relative to the cell to which they are connected. During the attack the user, as already mentioned, is unable to notice any anomaly because there is no trace of the SMS sent and received, not even in the message log.
To make the attack possible the software S @ T Browser – contraction of the SIMalliance Toolbox Browser – which has been defined by the SIM Alliance and is installed on a wide variety of SIM Cards (more precisely on the Universal Integrated Circuit Card) including eSIMs. It is a small software, not well known and now with a few years on its shoulders (it has not been updated since 2009), whose original purpose was, as mentioned, that of providing specific services to users by network operators . Although its functions have mostly been replaced by newer technologies, it is still operating behind the scenes as is the case with many legacy technologies. AdaptiveMobile Security noted that the S @ T Browser used by mobile network operators from at least 30 countries, thus affecting a total of over a billion individuals. However, it is likely to assume that other operators also still use this software for other specific SIM cards.
The researchers say that during the observation period they found how they are done per day Simjacker attacks primarily for tracking purposes towards 100-150 individuals, with peaks up to 300. It was found for a high variability in the number and frequency of attacks, with a model that suggests a specific surveillance activity, albeit applied to a large number of individuals , but not massively and with objectives and priorities that change over time.
Simjacker the first case of Malware-SMS
Although Simjacker has been used – at least according to the information disclosed by AdaptiveMobile Security – mostly for tracking purposes, the technique would actually allow take more or less profound control over the targeted device. Here are the commands you can run using Simjacker:
- PLAY TONE
- SEND SHORT MESSAGE
- SET UP CALL
- SEND USSD
- SEND SS
- PROVIDE LOCAL INFORMATION (including location, battery, network, and language)
- POWER OFF CARD
- RUN AT COMMAND
- SEND DTMF COMMAND
- LAUNCH BROWSER
- OPEN CHANNEL (CS BEARER, DATA SERVICE BEARER, LOCAL BEARER, UICC SERVER MODE, etc.)
- SEND DATA
- GET SERVICE INFORMATION
- SUBMIT MULTIMEDIA MESSAGE
- GEOGRAPHICAL LOCATION REQUEST
Devices of almost any manufacturer have proven to be vulnerable, precisely because the technique is not linked to a specific platform: the researchers cite by way of example Apple, Samsung, Google, Huawei, Motorola, ZTE and those who, as already mentioned, make IoT devices that contain SIM Cards. Some basic attacks (such as sending the IMEI code and geographical location) work indiscriminately on all devices, while others (for example the initiation of a call) only work on devices that do not require explicit confirmation from the user.
The Simjacker technique also represents a unique case in the panorama of cyber attacks against SIM Cards and mobile phones, since it can in all respects be classified as malware (spyware, specifically). In fact, malware is nothing but “bad” software, and software in turn is nothing more than a list of instructions. The fact that Simjacker gives exactly a list of instructions makes it actually the first real case of malware / spyware delivered directly via SMS. In all previous cases, sending malware via SMS always involved sending a link, not the malicious software built into the message.
What can we learn?
AdaptiveMobile Security has already communicated to GSM Association (the organization representing mobile network operators) the existence of the vulnerability, which is now managed through the GSMA CVD program which provides for the sharing of information in the mobile community. Direct consequence was the sharing of information with the SIM Alliance (which represents the main manufacturers of SIM Cards and UICC), which issued new security recommendations regarding the S @ T Browser.
The ball, at this point, in the hands of network operators who should check and block suspicious messages that contain commands aimed at the S @ T Browser and who should take advantage of the possibility of changing the security settings of the SIM Cards / UICC remotely, if not completely deactivate the S @ T Broswer technology (which, as we have said, outdated by more recent technologies). But in any case these are first steps, since from this episode it is necessary to draw a completely new way of considering the security of mobile communication networks.
We will never tire of repeating a key concept: safety is not a product but a process. We have pointed this out on many other occasions and will continue to do so as a broken record. Safety is a process whose strength is equal to that of the weakest link in its chain. Although often the weakest link is the end user (who is targeted in many ways, all the result of the most sophisticated and refined social engineering techniques), sometimes it happens, as in the case of Simjacker, that the weakest link in the chain is totally outside the end user domain.
It is for this reason that the approach security by design it must be the key priority in the world of technological development: think first about the security of a system (whether it is a technology, a software or a device), about the fact that it is intrinsically robust and resistant to threats, and following its functionality. Reverse the order (as has been done in past years in many of the technologies and devices we use today and as the vulnerability of S @ T Browser proves) reckless and dangerous especially in a reality in which the connection to a network is becoming a prerequisite essential for everything.
It therefore appears even more evident how adequately addressing the problem of IT security should translate into a major one collaborative effort by all the actors involved (companies, public, private, research) that contribute to building an ecosystem composed of knowledge, skills, solutions, procedures that lead to continuous and effective risk management, able to adapt more and more readily to the changing conditions of the world. Awareness first: prefigure the risks and threats that can fall on a technology, device, platform, company, user. Awareness the antidote to vulnerability.