In the middle of the oil crisis that has invested the markets in the past weeks and that is still not finding a solution, as evidenced by the negative prices reached in recent days by the May futures contract with WTI crude oil as the underlying (literally: a minimum of -40 $ on the evening of April 20), hackers have found a strategic target in the manufacturing companies.
It is the Bitdefender security company that tells a rather interesting story that dates back to the past weeks when the oil sector and the main producing countries were engaged in the negotiations which then led to the April 12 historic OPEC + decision to cut oil production by 9.7 million barrels per day in May and June, as an attempt to respond to the contraction in demand that occurred following the quarantine and social distancing measures adopted worldwide to combat the spread of COVID-19 pandemic.
Bitdefender has identified two spearphishing campaigns (an attack / scam that involves sending an electronic communication that has the purpose of stealing data or installing malware; the particularity of sending a message pretending to be a credible and authoritative sender) which has targeted companies operating in the energy sector and of oil & gas with the aim of installing a trojan to intercept confidential data and communications. The important aspect of both campaigns is the care with which the attack vehicle emails were built: in fact no typos or grammatical errors were detected which are often the distinctive feature of this type of campaign, and the contents of the two emails they present completely coherent, reliable and known elements to those operating in the oil sector.
Source: Bitdefender
The first of the two campaigns was found on March 31, with an email sent by a sender who took the form of Engineering for Petroleum and Process Industries (Enppi), Egyptian state company. In the email, the invitation for the recipient to make an offer for equipment and materials in the context of a real ongoing project, the Rosetta Sharing Facilites Project, on behalf of Burullus, a joint venture in the gas sector which in turn is owned by another Egyptian state company. Inside the email there were two attachments, masked by details on the conditions of the offer and forms to be filled out. The recipients of the email were 150 companies in the oil & gas sector: a rather limited number that demonstrates an accurate selection of targets, as opposed to those mass phishing campaigns that indiscriminately send counterfeit messages to tens of thousands of email addresses.
Source: Bitdefender
A second campaign, even more targeted, took place on the day of April 12th, this time addressed to companies operating in the maritime transport sector with ties always to the oil and energy sector. In this email a request is sent to fill in a document necessary for the operations of the tanker MT Sinar Maluku, which actually exists and flies the Indonesian flag and left its port on April 12 to reach its destination two days later. This email was sent to 18 companies, 15 of which operating in the transport sector in the Philippines.

The MT Sinar Maluku tanker, source: Vesseltracker
Both campaigns are united by an important element, which easily suggests that the hand behind them may be the same: in the attachments there is Agent Tesla, a malware-as-a-service that offers a very varied price list based on the different licensing models. It is a trojan that has been around since 2014 and offers a variety of features, including stealth techniques, persistence and security evasion, credential theft, data theft, screen copy and keylogging. Bitdefender notes that Agent Tesla, although already used in various campaigns, has never been used to specifically target realities related to the oil sector.
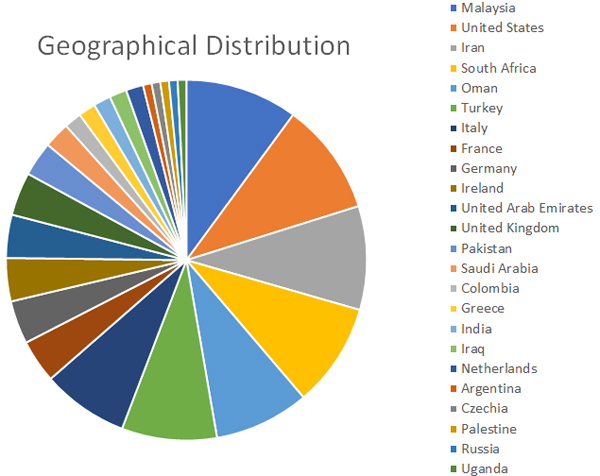
Countries affected by the March 31 campaign. Source: Bitdefender
Oil sector, but in general the energy sector, which certainly is not the first time that it is at the center of hacking campaigns. Last year it was subject to a significant number of attacks, and since September the trend has grown monthly, reaching a peak of over 5000 cases in February. Since the beginning of the year there have already been 13,000 attacks targeting the energy sector.
The malware used is not particularly sophisticated and certainly not at the level of those normally used in attacks aimed at high-level targets but despite the fact that no less than two campaigns of this type have been orchestrated and carried out in the specific time window prior to the decision of the 'OPEC + certainly suggests not one chance but one motivation and an interest in knowing specifically how certain countries were oriented in dealing with the oil crisis. Purpose? Difficult to say, but the desire to know in advance key information in situations of this type could be dictated by the interest in influencing the negotiation itself or in carrying out speculation operations enjoying an advantage of information asymmetry.
The two campaigns Bitdefender shed light on are excellent examples of how phishing attacks remain one of the most effective ways for attackers to get their first "foot in the door" of the targeted realities, despite the growing awareness that it is spreading on this kind of threats. Moreover, if phishing emails are successful, they continue to claim victims even when they contain grammatical errors, typing errors or "misplaced" elements, it is no wonder that they are successful when the contents are particularly accurate as has happened in these events.















