We are talking about BHI, a new type of vulnerability that affects most Intel and Arm CPUs. It seems that BHI re-enables Spectre-v2 exploits cross-privileged, allows kernel-to-kernel exploits (called intra-mode BTIs), and allows authors to inject prediction entries into the global branch prediction history to cause the kernel to leak data.
Unfortunately, the companies’ previous solutions for Specter V2 will not protect us from BHI, although AMD processors are mostly immune. Companies will need to release security patches soon.
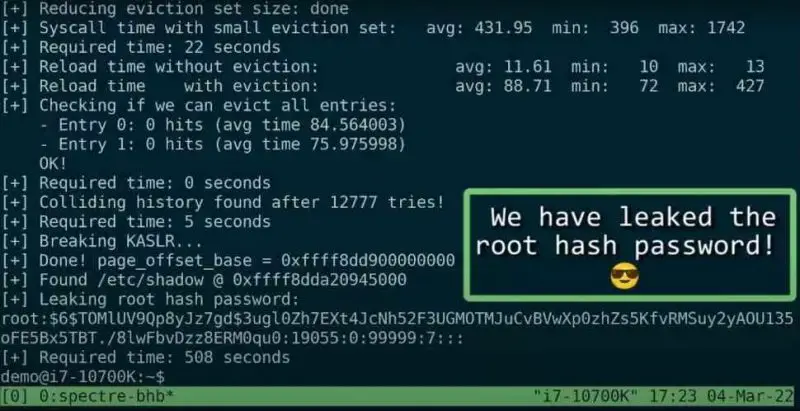
“The new exploit bypasses the elBRS mitigations in the case of Intel CPUs and ARM CSV2. This allows them to manipulate the kernel of the operating system through the CPU so that there are data leaks. Said in a summarized way and that everyone can understand, It is used to obtain confidential information, including private access codes of users.”.
Affected processors:
The vulnerability affects any Intel CPU released from Haswell, including Ice Lake-SP and Alder Lake. Affected Arm CPUs include Cortex A15/A57/A65/A72/A73/A75/A76/A77/A78/X1/X2/A710, Neoverse N2/N1/V1, and Broadcom Brahma B15.
En Linux:
Intel has released the following statement regarding the BHI exploit in the Linux community: “The attack, as demonstrated by the researchers, was previously mitigated by default on most Linux distributions. Intel’s recommendations have been implemented by the Linux community as of Linux kernel version 5.16 and are in the process of being retrofitted. “With the mitigation to previous versions of the Linux kernel. Intel released white papers describing more mitigation options for those using non-default settings and why LFENCE mitigation; JMP is not enough in all cases”.
With this, we should expect a patch soon from intel for the rest of the platforms.
AMD CPUs appear to be immune to BHI according to PhoronixRyzen processors that have the patch for Specter V2 should be safe.
Security patches from the other companies should be released soon. In addition to installing them, the researchers recommend disabling non-privileged eBPF support as an extra precaution.