Few are the people who have not suffered the unpleasant experience that one of your accounts has been hacked, whether from email, from a social network, from a streaming service … As we have been using more and more online services of all kinds, the number of access credentials managed by each user has grown to the point of becoming in a complication. A complication that, on many occasions, gives rise to undesirable habits.
Thus, when a leak occurs and, as a result of it, one of our accounts is hacked, we can face a much bigger problem if, for example, we have recycled passwords, or we use a very similar password, with small variations between services. In this way, one hacked account can become many, and you can imagine the problem that this poses.
However, How to find out if any of your accounts have been leaked and could be hackedBefore that can turn against you? And what can you do in such a case?
Have any of your accounts been hacked?
There are several ways to check if any of your accounts in online services have been hacked. Unfortunately, in many cases the worst is the one that corresponds directly to the service that has suffered the leak. And is that, as a general rule, communications by services when they suffer a leak are usually terribly generic, and do not inform each user individually about whether their specific account has been compromised or not,
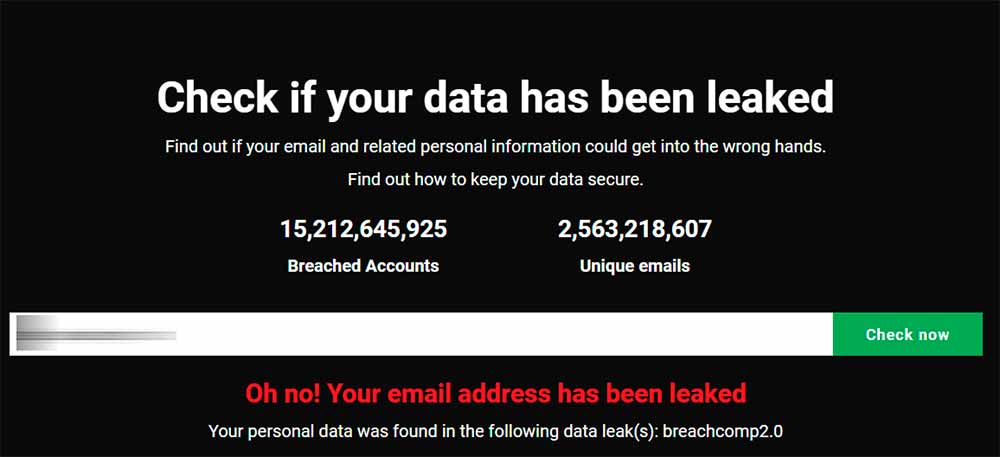
Fortunately, there are services that collect leaks and allow users to check if their accounts have been affected. The most popular of them is undoubtedly Have I been pwned? For years collect leak listings, and with its search function it allows us to check if records have been found with our email address. If any of your accounts has been hacked, it is most likely that their data has come from one of the lists maintained by this website.
Its operation is very simple. You just have to write your email address, and in case it is found in any of the leaks collected, you will see a warning message along with the leaks in which it appears
Although it shows less information, at least for the moment, another very interesting option in this regard is the service launched by Cybernews. Based on the largest collection of credentials obtained from leaks and security breaches, and which includes no less than 3,200 million combinations of email and password, it allows us to check if our email accounts appear in any leak and if, therefore Therefore, those accounts can be hacked.
Its operation is similar to that of Have I been pwned ?, you just have to write your email address and, in case there is any result, you will see a message informing about it, and in which it is mentioned in what leakage or leaks appear
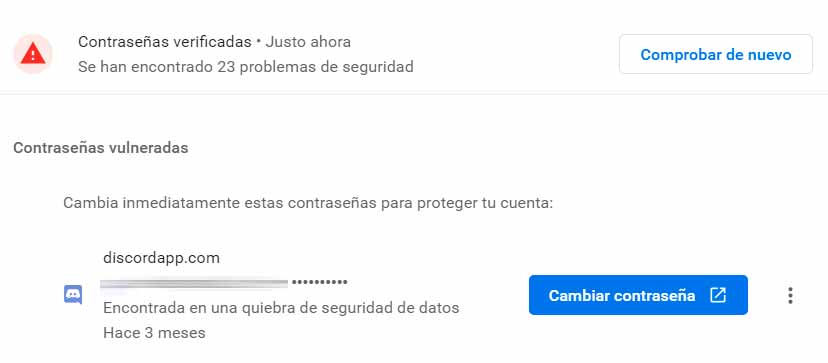
In case you use your browser’s password manager, some of them have a verification function, which checks the accounts that you have stored in it, and indicates which of them have been compromised and, therefore, they can be hacked. Access the manager and, if it has such a function, you will be able to find information, as in this case of Google Chrome, about each of the compromised accounts
How to deal with a hacked account?
If after performing any of these checks you discover that one of your accounts has been compromised, reaction speed is a key element. The sooner you act, the less risk you expose yourself. Although it varies from service to service, there are several key recommendations, which you should follow immediately, that will minimize the risk of your accounts, data, and more falling into the wrong hands.
Strong passwords: Media and professionals have been focusing on this point for years and yet, surprising as it may seem, tremendously insecure passwords continue to be used, as we have been telling you year after year. That the accounts that use them are hacked is only a matter of time and, although it is ugly to blame the victims, in these cases the truth is that they will be making it easier for the attackers.
Fortunately, for some time now the services are beginning to impose certain security measures on the keys: a minimum length, combinations of uppercase, lowercase and special characters, change of password with prohibition of recycling them, and so on. It is best to internalize these measures and use them whether or not it is mandatory in the services. Using passwords that are neither simple nor deductible (children’s names, birthday dates, etc.) are the first and fundamental security barrier.
Unique passwords: Using the same password in two or more services is a more serious security problem than you might think. And it is that if using the same credentials (same email account and same username) in, for example, ten services, it is enough that one of them is compromised and suffers a leak so that the security of the ten accounts is seen engaged.
Although the level of risk is reduced, it is also not recommended to use similar passwords with, for example, a text string that is repeated in all, and a number at the end that makes them not the same. And it is that if an attacker sees a key like Duckling3, it will not take too long to try with Duckling01, 2, 4, and so on.
Renew passwords: That we have news of some leaks does not mean that we have news of all leaks. And even in the best of cases, sometimes it takes years from when the breach occurs until it is made public. And if we talk about an account hacked by other methods, we may never know that our password has fallen into the wrong hands. It will depend, mainly, on the way in which it is used by the attacker.
Therefore, given the risk that our credentials have been compromised and we do not know it, it is best to change the passwords regularly, increasing the frequency based on the level of protection that we consider necessary for each service. And it is that a free account in a service in which we do not have associated means of payment is not the same as an access to electronic banking. The greater the need for protection, the greater the frequency of password change.
Password manager: Managing such a vast and ever-changing catalog of complex passwords may not be humanly possible, and indeed, if we employ truly strong passwords, only a very, very privileged brain would be able to remember them. Thus, instead of doing excessive mental exercises, it is best to use a password manager.
You can opt for services that have clients for the main operating systems for computers and mobile devices, or for solutions to install on your PC and manage them from there. Or if you prefer, as I mentioned before, more and more browsers offer this function.
Two-step verification: Today this is undoubtedly the Holy Grail of user account protection. Whether through SMS message, app, validation code or other measures, combining a secure password with a unique code obtained by another means or validation from other devices can protect you from 99 out of 100 attacks. Not surprisingly, many services enable this function, and even make its use mandatory, when they have suffered a data leak. It is much more difficult for an account to be hacked if 2FA authentication is used.