Millions of Lenovo Devices Affected by BIOS Vulnerability
Millions of Lenovo laptops are affected by a serious BIOS vulnerability. Lenovo informed its customers about the vulnerability on its support website this week. The company has already released firmware updates for some of the affected devices and plans to release the remaining updates in early May.
Lenovo discloses on the website that several of its portable devices are affected by three different vulnerabilities: CVE-2021-3970, CVE-2021-3971, and CVE-2021-3972, which could allow attackers with elevated privileges to execute arbitrary code. or disable SPI flash protections during OS runtime.
ESET, the security company that discovered the vulnerabilities and reported them to Lenovo, found that two of the vulnerabilities affect UEFI firmware drivers that were intended only for use in the manufacturing process. It appears that Lenovo did not properly disable them on production devices.
Affected Devices and Firmware Fixes
The vulnerabilities affect multiple families of Lenovo devices, including Lenovo IdeaPad 3, Flex 3, L340, Legion 5 and 7, Legion Y540, S14, S145, S540, Slim 7 and 9, V14 and V15, and Yoga Slim 7 devices. The complete list of affected devices is available on the Lenovo support website.
Lenovo has released updated firmware versions for some of the affected products. For others, it aims to deliver firmware updates on May 10, 2022. Devices that have reached end of service will not receive firmware updates.
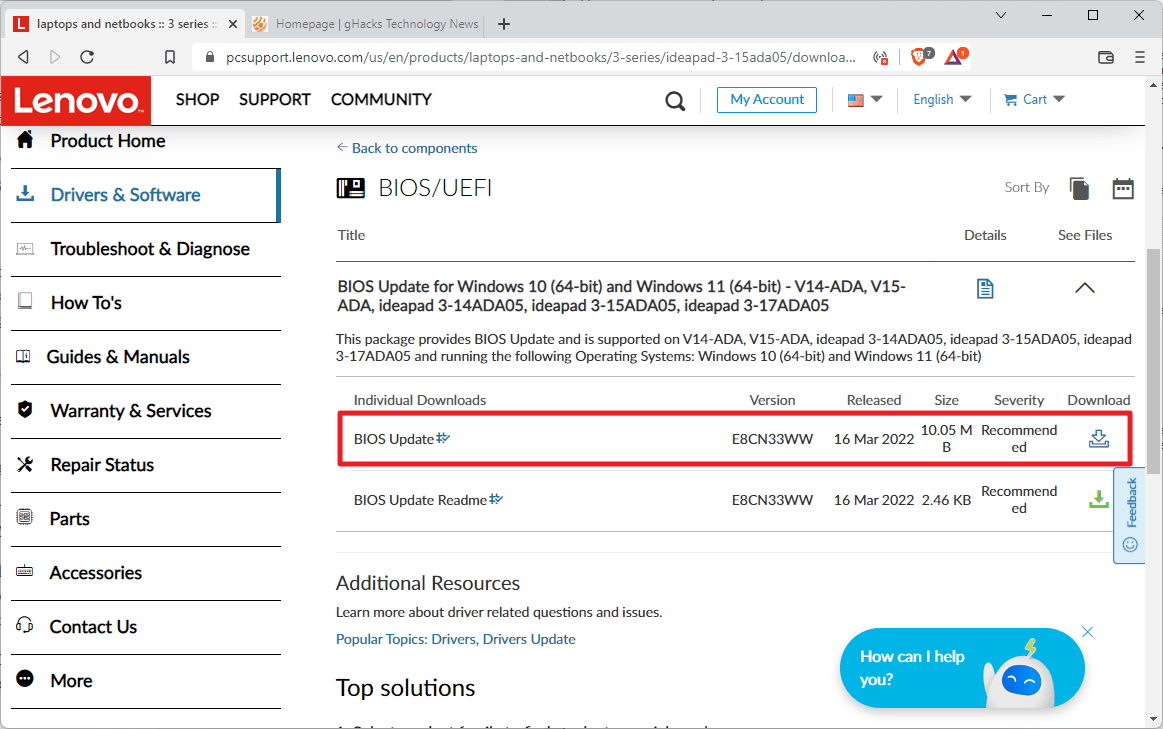
Some devices are not affected by all three vulnerabilities, but most are affected by all three confirmed vulnerabilities. Lenovo provides updated firmware drivers; customers should click the device support link on the Lenovo website to open the driver website.
There, they should select BIOS/UEFI to display available firmware updates to download the update. The support page, which lists the vulnerabilities, lists the firmware versions that contain the security fixes.
Updates can be installed directly from the Windows operating system by running the downloaded executable file. A readme file is available for each firmware file, which provides instructions on how to install the update on the device.
Customers can also visit Lenovo’s main support website to check for updates for their devices in this way.
Analysis of vulnerabilities in Lenovo laptops
Security company ESET reported the vulnerabilities to Lenovo in October 2021. Lenovo confirmed the vulnerabilities in November 2021 and requested to postpone the public disclosure date to April 2022. Lenovo published the security advisory on April 18, and ESET published its findings. and details a day later.
The CVE-2021-3971 vulnerability can be exploited to disable SPI protections on Lenovo devices. UEFI firmware is typically stored on a flash memory chip built into the computer’s motherboard. It is connected to the processor through the serial peripheral interface (SPI).
The memory is independent of the operating system, which means that it remains even if the operating system is reinstalled or another system is installed. An administrator could wipe a device’s hard drive, install another operating system, and the acquisition would not change the memory. Since it is non-volatile, it is a high-level target for threat actors.
Malware such as LOJAX, the first UEFI rootkit found in the wild, MosaicRegressor Lunar Bounce, targeted memory in attacks.
Manufacturers have created various security mechanisms to protect SPI flash from unauthorized modification. The main line of defense is “provided by special memory-mapped configuration registers exposed by the chipset itself: the BIOS control register and five range-protected registers.”
CVE-2021-3971 can be exploited by creating the NVRAM variable. Successful exploitation disables SPI flash write protections. With the variable set, the platform firmware will skip execution of the code that is “responsible for configuring the BIOS control register and protected range register-based SPI flash protections.”
The attacked system allows the SPI flash to be modified, even when executed from non-SMM code, allowing attackers to write malicious code directly into the firmware storage. SMM, System Management Mode, is used for various tasks, including safely updating a device’s firmware or running proprietary code by OEMs.
ESET notes that any Windows administrator, with the SE_SYSTEM_ENVIRONMENT_NAME privilege, can exploit the vulnerability using the “SetFirmwareEnvironmentVariable Windows API function.”
The CVE-2021-3972 vulnerability gives attackers control over various UEFI firmware configurations. These include UEFI Secure Boot status or the ability to restore factory settings. Attackers can exploit the security issue for various tasks, including disabling Secure Boot on the device.
Secure Boot is part of the UEFI specification. Its main purpose is to verify the integrity of the boot components to ensure that the components can be executed. Secure Boot uses databases to determine trusted components. UEFI drivers, applications, and third-party OPROMs are generally verified, while drivers in the SPI flash are “implicitly considered to be trusted.”
Disabling Secure Boot, and thus disabling its component verification process, allows any component, including untrusted or malicious components, to load during boot. Resetting UEFI firmware to factory defaults can also have serious consequences, especially if it would lead to loading components with known security vulnerabilities.
An attacker needs to set a UEFI variable on unpatched Lenovo devices to exploit the vulnerability. A Windows administrator account with the SE_SYSTEM_ENVIRONMENT_NAME privilege is required to carry out the attack during the operating system runtime.
The third vulnerability, CVE-2021-3970, was discovered by ESET during the company’s investigation of the other two vulnerabilities. The vulnerability allows arbitrary read and write operations to and from SMRAM; this can lead to “malicious code execution with SMM privileges” and potentially “deployment of an SPI flash implant”.
closing words
Lenovo has released a security advisory describing the three vulnerabilities and affected devices, and firmware updates for most of the affected devices. Customers are encouraged to update the device firmware immediately to protect the device against exploit-targeted attacks.
Some devices will receive the firmware update on May 10, 2022. These will remain vulnerable until at least that date. Customers may want to check the support page again on the date to download and install the update on their devices.
Several Lenovo devices will not receive firmware updates. ESET recommends using a “TPM-compliant full disk encryption solution capable of rendering data on the disk inaccessible if you change the UEFI Secure Boot setting.”
advertising